You just updated your laptop with the latest virus definitions and security patches and you think, “there we go, I’m safe now!”
Unfortunately, that’s not necessarily true. Cybercriminals and hackers are always thinking of clever, new ways to exploit your devices— and you have to be perpetually vigilant.
Malware threats, in particular, are quite dangerous for businesses and individual users alike, and there’s a new attack to look out for: the USB Ninja Cable.
In this post, we’ll cover what this malware-infecting method is, what to look out for and how to protect your business from being exploited.
What is the USB Ninja Cable?
A USB Ninja Cable is a USB cable designed to infect connected devices with malware. This malicious cable works by injecting keystrokes onto your computer upon being plugged into a USB-friendly device.
These keystrokes allow the attacker to download malware and infect your device, oftentimes by gaining remote access to your private files.
What Could the Hacker Do Afterwards?
Malware is malicious software intentionally designed to cause damage to your device or network. It comes in many forms, including computer viruses, worms, Trojan horses, ransomware, spyware, adware, etc.
The USB Ninja cable can be designed to carry many forms of malware, all with different impacts. One example may involve the bad actor gaining exclusive access over your private documents and files, and holding them for ransom until you pay to have them released. This “ransomware” attack is a common practice and, if paid, becomes quite profitable for hackers, but very costly for your business.
How Can You Tell a Ninja Cable Apart from an Ordinary USB Cable?
That’s the scary part— you can’t. A USB Ninja Cable looks and feels just like any ordinary USB cable. There’s no clear way of determining if it’s an infected cable simply by holding it in your hand.
When plugged into your device, the Ninja Cable acts just like any other USB in functionality too. For instance, in Kevin Mitnick’s live demonstration video shown above, you’ll see that when plugging a phone into the computer, the USB cable still allows the phone to charge. Because of this, many are none-the-wiser that there’s a problem with the cord.
Won’t You See the Attack Happening?
The injected keystrokes that infect your computer with malware can be set to activate when the device is inactive for a given period of time (let’s say, 5 minutes after sitting idle, whereas the hacker assumes you have left the device unattended), and run a quick, 5-second command to infect your computer.
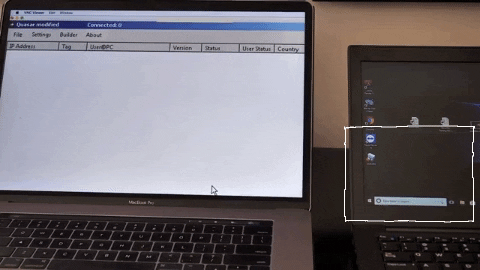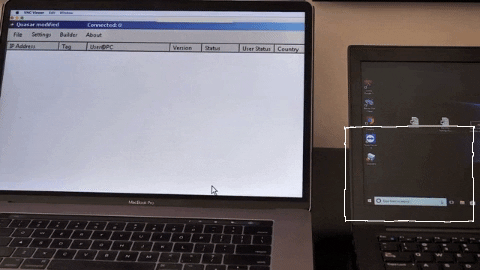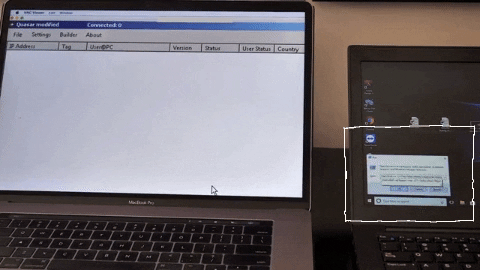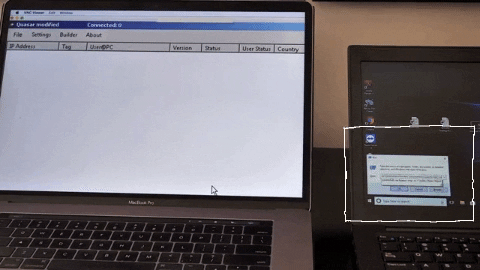
The keystroke injection can run so quickly, it’s easy to miss. That’s why this USB exploit is so dangerous: it’s super effective and almost undetectable.
How Can You Protect Yourself?
Although you can’t tell a Ninja USB Cable apart from a normal USB cord, there are a few things you can do to avoid this type of malware injection:
1. Know it’s not just USB cables.
Cybercriminals can also corrupt other forms of device cables, like USB-A and USB-C cords, micro USBs, lightning cables, USB sticks (aka flash drives), etc. They can even weaponize a computer mouse with a cord that plugs into your USB.
2. Know that no device is safe from infection.
Some users think that Macbooks are impossible to hack, or that their PC with antivirus software is safe. This is not true, all devices can be vulnerable to a Ninja USB Cable attack.
3. Keep up with the ever-changing threat landscape.
Cyber threats are always changing, as hackers get more and more creative with their exploits. It’s crucial to stay up-to-date with new threats, like the USB Ninja Cable and beyond.
4. Give your staff security awareness training.
The right cybersecurity team can provide your team with helpful insights to ward against malicious malware threats. Some things an expert in security awareness can teach your staff include never use the same password across multiple websites, never plugging in devices you don't know the origin of, never throwing away data or drives, etc. (A good place to start educating your staff is by assigning them one of these cybersecurity books to read).
Stop, Look & Think
The best thing you can do to avoid a USB Ninja Cable attack is to “stop, look and think” before you plug in any device.
It’s easier than you might think to sneakily replace an ordinary cable with an infected USB Ninja lookalike. For instance, a “new-in-the-box” phone cable could be pre-wrapped to look like it came in that packaging, but was really replaced prior to giving new work phones to new hires.
Your data is facing more risks than ever before and it’s increasing every day. So it’s crucial to seek expert advice on protecting your assets.
Live Demonstrations & Awareness Training with Kevin Mitnick
Show your team what a USB Ninja Cable attack looks like in-person, with a live security awareness demonstration from the world’s most famous hacker: Kevin Mitnick. Mitnick is a whitehat “Classified Threat Demonstrator” who can educate your team on best practices for threat mitigation. Book Kevin as a keynote speaker today.




